Security related topics in distributed systems
Common types of security threats
Leakage: Unauthorized access to data or service (Confidentiality)
Tampering: Unauthorized modification to data or service (Integrity)
Vandalism: Interference with normal service. (Availability)
Policy of security
Confidentiality, Integrity, and Availability together means CIA properties, which is security policy (what we want to achieve).
Common types of attacks
Eavesdropping: attacker taps into networks
Masquerading: attackers pretend to be someone else
Message tampering: attacker modifies messages
Replay attack: attacker replay old messages
Denial of service: bombard a port
Mechanisms of security
Mechanisms, on the other hand, is how we implement the security techniques to achieve security policies.
Authentication: is a user really the user?
Authorization: is the user allow to do so?
Auditing: keep checking what a user is doing
Cryptography in mechanism
Key: sequence of bytes assigned to a user, one can lock/unlock only when with the same key. No one can decode an encoded message without the key.
There two sub-category;
- Symmetric key systems: basically meaning same key used to both encrypt and decrypt a message. And the key is shared between sender and receiver.
- Public-private key system: everyone has two key: public key(everyone knows), private key(only the user knows). Anything encrypted with A’s private key can decrypted only with A’s public key. Anything encrypted with A’s public key can decrypted only with A’s private key.
Cryptography in Authentication
For authentication purpose, we use key and encrypt/decrypt message to assure identities. There are two flavor to do so:
- Direct authentication
- Indirect authentication
Direct authentication:
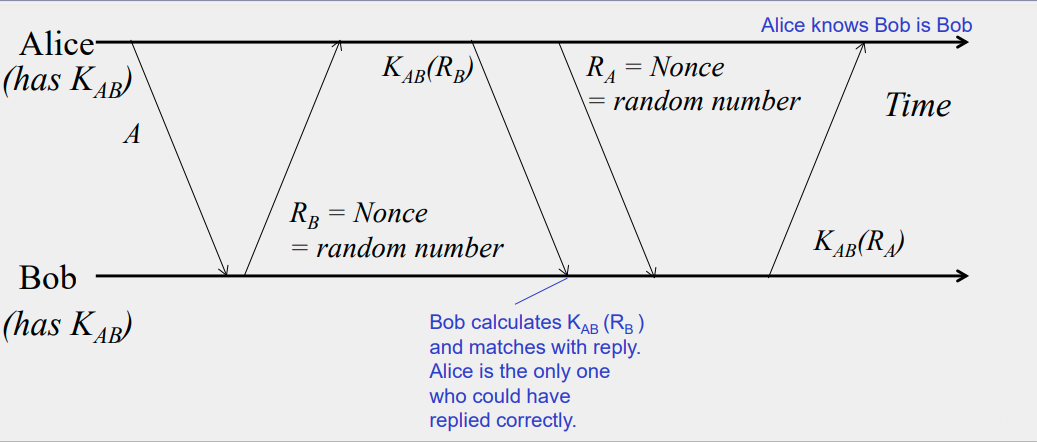
Indirect authentication:
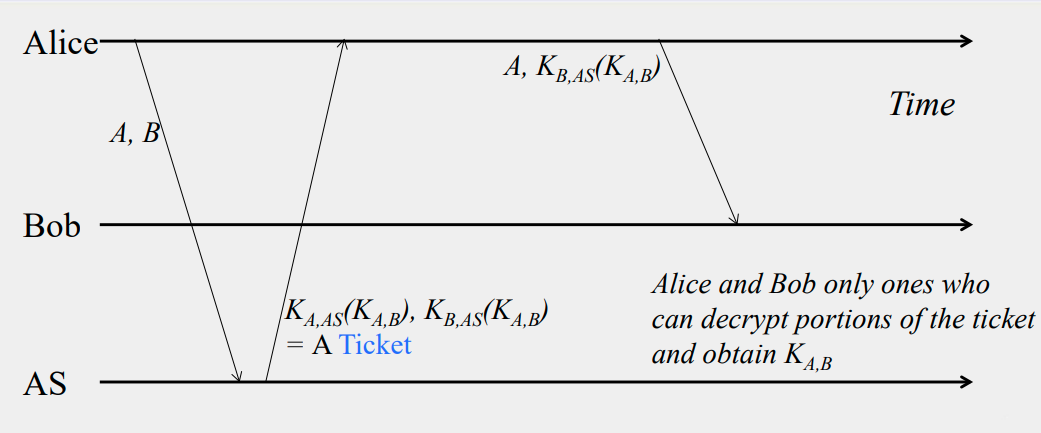
Cryptography in Digital Signature
To sign a message M, one should send M along with the encrypted version of M using private key, so that everyone can use sender’s public key to verify it.
Cryptography in Digital Certificate
Similar to digital signature, it uses chain-like signature to generate chains of certificates
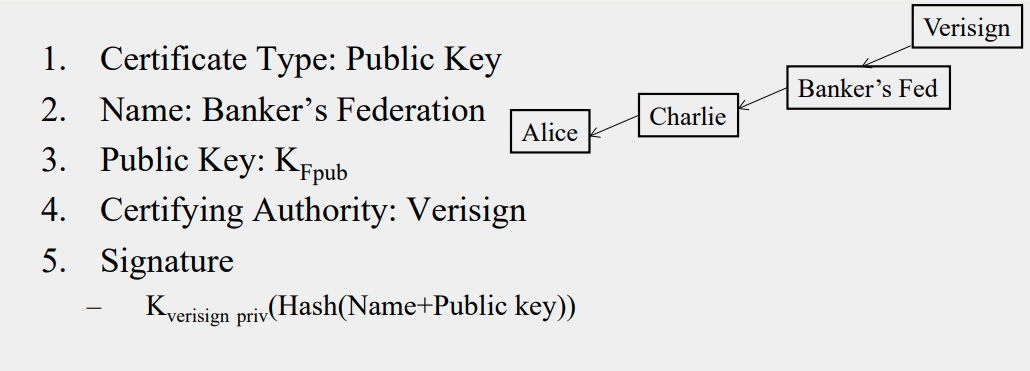
- 本文作者: Yu Wan
- 本文链接: https://cyanh1ll.github.io/2021/01/19/distributed-system-security/
- 版权声明: CYANH1LL

